Some months ago, in my quest to look at different methods for obtaining an access token interactively for Microsoft Graph in PowerShell, I wrote a simple PowerShell wrapper around the Microsoft.Identity.Client library, aka MSAL.Net – the supported MS library for authenticating with Microsoft Entra. Microsoft’s apps and modules have been trending toward using the Web Account Manager (WAM) in Windows to authenticate, so I spent some time looking at how this can be done in PowerShell. WAM is an authentication broker that can deal with access tokens for accounts already connected to your Windows device. According to Microsoft, this has several benefits:
- Enhanced security. Many security enhancements will be delivered with the broker, without needing to update the application logic.
- Feature support. With the help of the broker developers can access rich OS and service capabilities such as Windows Hello, conditional access policies, and FIDO keys without writing extra scaffolding code.
- System integration. Applications that use the broker plug-and-play with the built-in account picker, allowing the user to quickly pick an existing account instead of reentering the same credentials over and over.
- Token Protection. WAM ensures that the refresh tokens are device bound and enables apps to acquire device bound access tokens
Figuring out how to use WAM in PowerShell was a more challenging endeavour than I anticipated though! Similar to before, I wrote wrapper code around the Microsoft.Identity.Client library, but this time it didn’t play so well. The main hurdle I couldn’t overcome was that to use the WAM broker, it is necessary to call an extension method on the PublicClientApplicationBuilder called “WithBroker”. This method exists in the Microsoft.Identity.Client library, however the method that works with the WAM broker is in a separate library – Microsoft.Identity.Client.Broker. No amount of my trying could get PowerShell to use this extension method instead of the native one. Probably at some point this extension method will find its way into the main library, but until then the only way I could make this work was to port some C# code into PowerShell.
Porting code had its own challenges, as it was necessary to figure out which dependent assemblies the code needed to reference.
Long story short, we have some working code finally 🙂 As before, it requires the Az.Accounts module to be installed because most all the required libraries are already present in this module, negating the need to download them separately. It also only works in PowerShell Core (sorry .Net framework lovers!)
Since my most common use for this is to get an access token for Microsoft Graph, I set the default client Id (aka app Id) to that of the Entra app created by the Microsoft Graph PowerShell SDK, and the default scope to “https://graph.microsoft.com/.default”, but you can change these values to other app Ids and scopes as required, for example to get an access token for Azure SQL database using the Azure CLI or Azure PowerShell apps (another use case of mine!)
To use WAM, the Entra app you use does need to have the following redirect URL added:
ms-appx-web://microsoft.aad.brokerplugin/<appId>
A tenant Id is not required so that the Windows-native account picker will display and allows you to select from any work or school or Microsoft accounts connected to Windows.
One thing to note about this account picker is that can sometimes appear behind the current window, or even on a different screen, so do check if it seems nothing is happening. Hopefully Microsoft will fix that at some point.
Once an access token is obtained, it will be cached. This makes it much faster to retrieve the access token again in the same session. When a token has expired, it will be refreshed on the next token request in the same session.
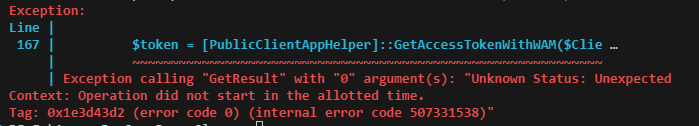
One small bug is that if you try to request an access token for a different client Id or scope in the same session, it may error with the following. I haven’t yet figured out why this happens 😳
Here are a couple of example for how to use it:
# Obtain an access token for the Microsoft Graph API using the Microsoft Graph PowerShell SDK app
Get-EntraAccessTokenWithWAM
# Obtain an access token for the Azure SQL Database using the Azure CLI app
Get-EntraAccessTokenWithWAM -Scopes "https://database.windows.net/.default" -ClientId "04b07795-8ddb-461a-bbee-02f9e1bf7b46"
# Obtain an access token for the Azure SQL Database using the Azure PowerShell app
Get-EntraAccessTokenWithWAM -Scopes "https://database.windows.net/.default" -ClientId "1950a258-227b-4e31-a9cf-717495945fc2"
And here’s the code 👍